Download PDF
Download page Configure Single Sign-on Through SAML.
Configure Single Sign-on Through SAML
This page provides instructions for configuring Single Sign-on (SSO) through Security Assertion Markup Language (SAML).
You can configure an Identity Provider (IdP) to enable single sign-on access to your Splunk AppDynamics environment. Splunk AppDynamics can authenticate and authorize users through the Cisco Customer Identity or an external SAML 2.0 protocol IdP. The Cisco Customer Identity will enable users to reuse an existing Cisco Identity and redirect them to the Cisco Identity Provider (IdP) when signing in.
Refer to the documentation of your identity provider for detailed configuration instructions. See Configure SAML Authentication for the Identity Provider.
This document uses the term Tenant to refer to both a Observability Platform tenant and a Controller Tenant.
Supported Identity Providers
Splunk AppDynamics certifies support for the following IdPs:
- Okta
- Onelogin
- Ping Identity
- Azure AD
- IBM Cloud Identity
- Active Directory Federation Service (AD FS)
Other IdPs supporting HTTP POST binding are also compatible with Splunk AppDynamics SAML authentication. If you are having issues setting up SAML with your IdP, contact Splunk AppDynamics customer support for help.
Configure SAML Authentication for the Identity Provider

SAML Settings for the Identity Provider
Your identity provider requires information about your account for the SAML settings. The <domain> is the domain of your
Observability Platform tenant, but doesn't apply to all SaaS Tenants.
| Setting | Description |
|---|---|
| Issuer ID (Service Provider Entity ID) | The unique identifier intended for the SAML assertion. In most cases, it is the Service Provider Entity ID, unless the Service Provider decides to use a different identifier.
|
| Single Sign-On URL (Assertion Consumer URL) | The Splunk AppDynamics endpoint to service SAML Authentication. You need to specify your Splunk AppDynamics account name with the query string parameter accountName as shown with the following syntax and example:
|
SAML Attributes for the Identity Provider
You set attributes with your identity provider to map attribute values to Splunk AppDynamics SAML users. Once the attributes are set, the Splunk AppDynamics Account Administrator can view the attribute values mapped to a user from the Account Management Portal. In addition, Splunk AppDynamicsusers may also see the mapped attribute values in their mini profiles of the Observability Platform tenants.
The following table shows how IdP example attributes map to the First Name, Last Name, and Email attribute settings of a SAML user:
| Example Attribute Name | Example Attribute Values | Description |
|---|---|---|
| First Name | Jane | Informal name for the user corresponding to the AppDynamics |
| Last Name | Doe | Informal name for the user corresponding to the AppDynamics lastName field. |
| Jane.Doe@company.com | User's email address corresponding to AppDynamics e |
JIT Provisioning
Administrators can initiate JIT provisioning of users through the IdP or the Service Provider (Splunk AppDynamics Accounts):
- JIT-initiated by IdP: Administrators configure SAML authentication, and users visit the IdP and click a link to the Splunk AppDynamics Accounts to self-provision their user accounts.
JIT-initiated by Splunk AppDynamics Accounts: Administrators configure SAML authentication and generate a JIT-provisioning link that can be shared with users to self-provision their Splunk AppDynamics accounts. When team members sign in using this link, their user profile with Community and training access will be auto-created for them.
The JIT provisioning link will only work if SAML federation is active and is entirely optional: Splunk AppDynamics Administrators can still manually create user profiles.
In addition, when setting up SAML from Splunk AppDynamics Accounts, Administrators can also select which Observability Platform tenants to provision for those signing in with the JIT-provisioning link. For security reasons, the JIT-provisioned users are assigned to a read-only role, so you'll need to manually update the roles of JIT-provisioned users. See Assign Tenant Roles.
Configure SAML Authentication
The processes described vary slightly based on your choice to upload your IdP data or to enter it manually.
The following two flows make it easier for you to configure SAML and reduce the need to go back and forth between your IdP and Cisco AppDynamics:
Configure your IdP with AppDynamics
(1) Select Setup Method
Select Configure your IdP in AppDynamics.

- Click Next.
(2) Provide IdP Metadata
Click Upload metadata to upload the IdP metadata from your local drive or manually enter/select values for the following fields:
Single sign-on URL - (SSO URL) A unique URL allowing users to access multiple applications and services with one set of login credentials.
- X.509 Certificate - A digital certificate using the X.509 standard to verify the identity of a person, organization, or device in a secure and encrypted manner.
- Issuer ID - A unique identifier assigned to the entity that issues a digital certificate. It helps to verify the authenticity of the certificate and trace its chain of trust back to the root certificate authority.
- Request Binding - The HTTP method to send an authorization request to an authorization server.
Confirm that each of the fields has been completed and click Next.

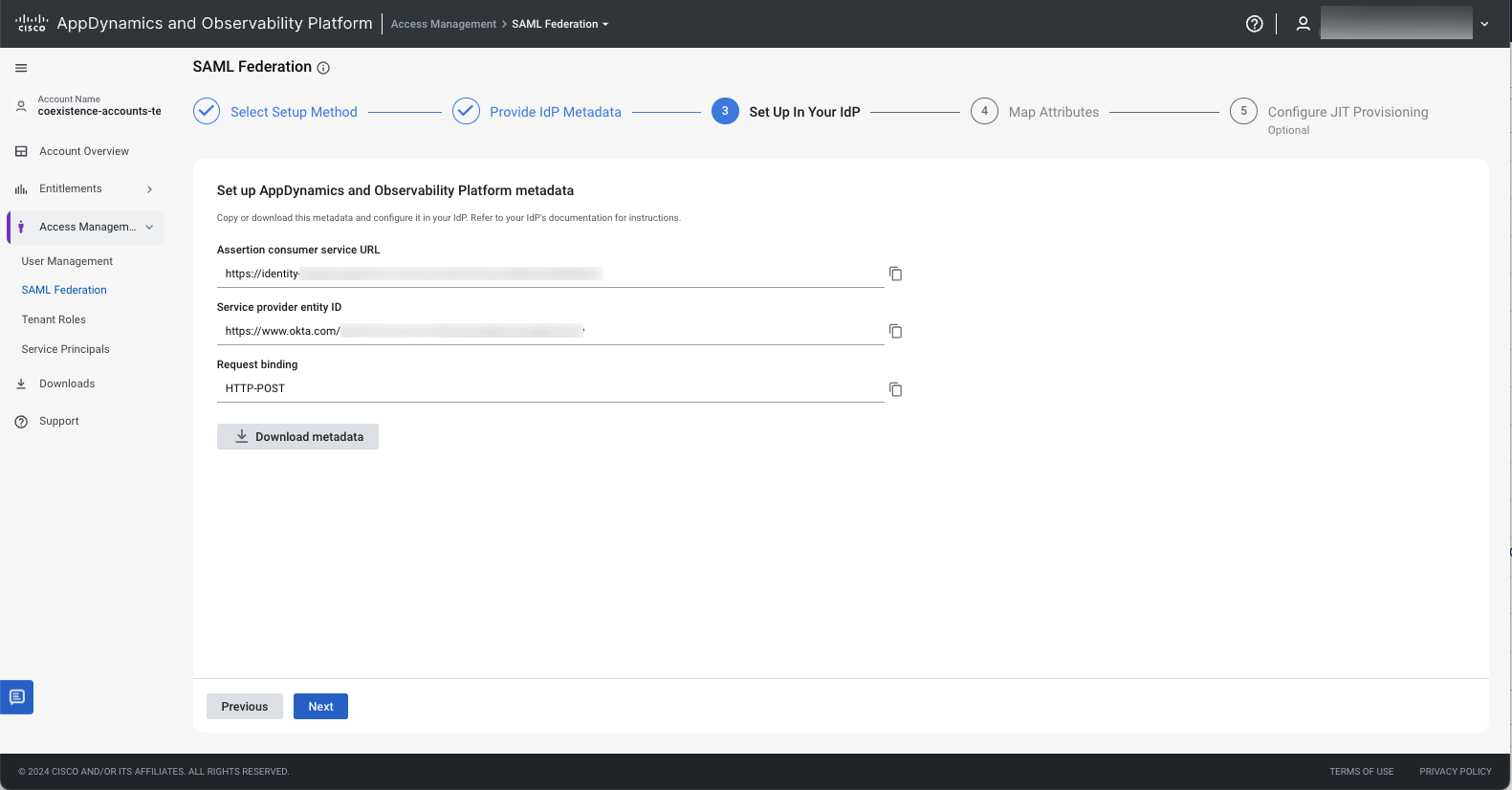
(3) Set Up In Your IdP
From Set up AppDynamics metadata in your IdP, enter values for the following fields:
- Assertion consumer service URL - The URL where a web service provider receives authentication assertions from an identity provider during SSO.
- Service provider entity ID - The unique identifier (URL) for the service provider in a SAML (Security Assertion Markup Language) transaction.
- Request binding - The HTTP method to send an authorization request to an authorization server.
Confirm that each of the fields has been completed and click Next.
(4) Map Attributes
From Map your IdP attributes to AppDynamics attributes, enter attributes from your IdP and the corresponding attribute values for Cisco AppDynamics. For example, you might map the IdP attributes fname, lname, and email to the Cisco AppDynamics attributes First Name, Last Name, and Email.
- Click Next.
(5) Configure JIT Provisioning (Optional)
- Select the Tenants you want to provision by default.
Click Save.

Copy and share the JIT provisioning link with members of your organization needing an Splunk AppDynamics user profile with Community and training access.
Configure AppDynamics in your IdP
(1) Select Setup Method
Select Configure AppDynamics in your IdP.

Click Next.
(2) Set Up in Your IdP
From Set up AppDynamics metadata in your IdP, enter value for the following fields:
- Assertion consumer service URL - The web address (URL) used by your service provider (SP) to receive and process authentication information (SAML response) from an identity provider (IdP).
- Service provider entity ID - The web address (URL) of a service provider (SP) used by the identity provider (IdP) to identify and establish trust with the service provider (SP).
- Request binding - The HTTP method to send an authorization request to an authorization server.
Confirm that each of the fields has been completed and click Next.

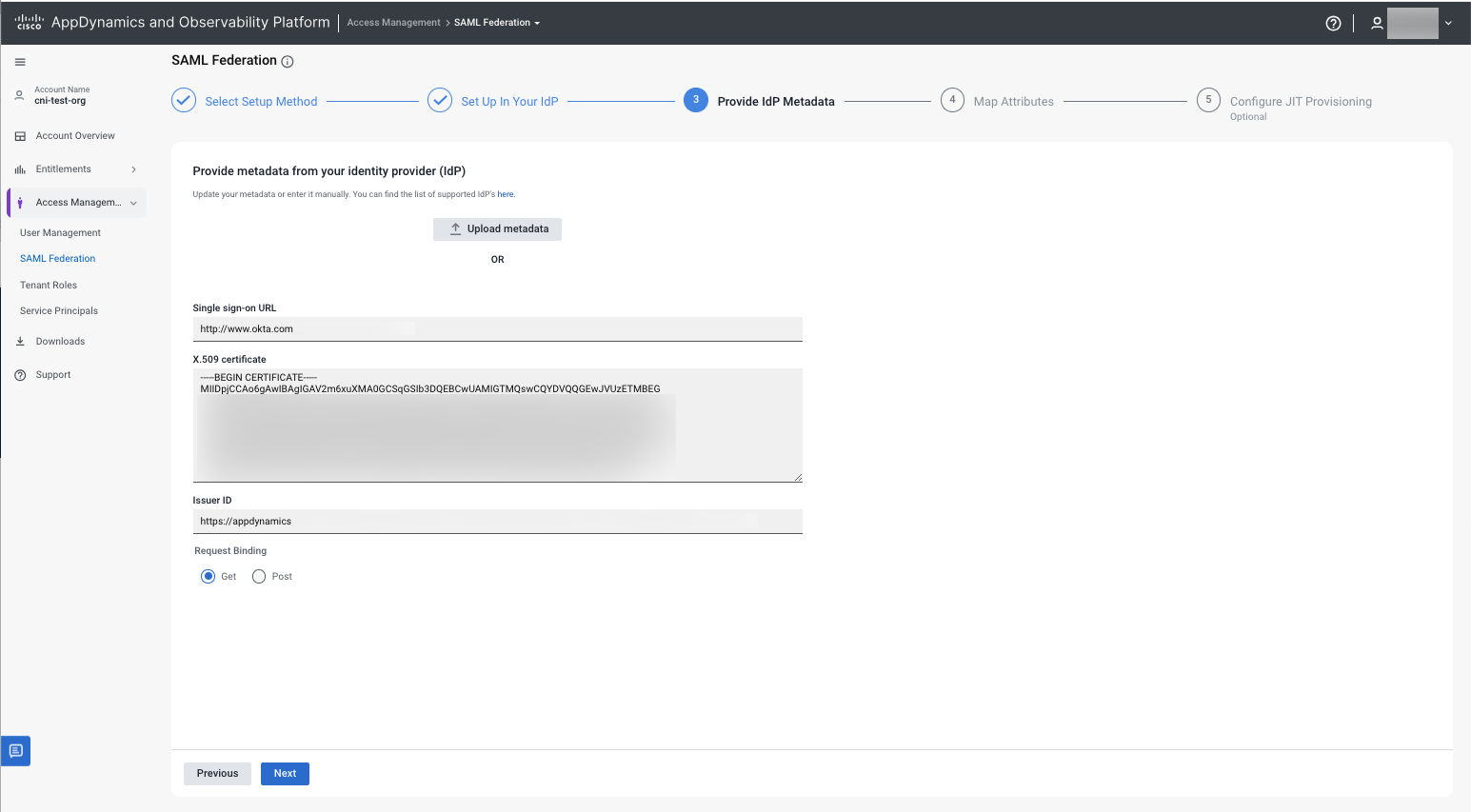
(3) Provide IdP Metadata
From Provide metadata from your identify provider (IdP):
From Upload metadata, click the empty field and select the metadata file from your local drive.
OR- Enter the IdP details:
- Single sign-on URL - (SSO URL) A unique URL allowing users to access multiple applications and services with one set of login credentials.
- X.509 certificate - A digital certificate using the X.509 standard to verify the identity of a person, organization, or device in a secure and encrypted manner.
- Issuer ID - A unique identifier assigned to the entity that issues a digital certificate. It helps to verify the authenticity of the certificate and trace its chain of trust back to the root certificate authority.
- Request binding - The HTTP method to send an authorization request to an authorization server.
Confirm that each of the fields has been completed and click Next.
(4) Map Attributes
From Map your IdP attributes to AppDynamics attributes, enter attributes from your IdP and the corresponding attribute values for AppDynamics. For example, you might map the IdP attributes
fname,lname, andemailto the AppDynamics attributes First Name, Last Name, and Email.- Click Next.
(5) Configure JIT Provisioning (Optional)
- Select the Tenants you want to provision by default.
Click Save.

- Copy and share the JIT provisioning link with members of your organization needing an Splunk AppDynamics user profile with Community and training access.
You can now also map users to the SAML IdP through User Management. See Create a New User.
Verify SAML Authentication Configuration
To verify that you configured SAML authentication correctly, navigate to accounts.appdynamics.com.
If you chose to authenticate through your IdP, the sign-in screen asks for your email and redirects you to your IdP for authentication.
If you chose to authenticate through AppDynamics, the sign-in screen requests your email and password.
Update or Fetch SAML Configuration
After successfully configuring SAML, you can update your IdP metadata, attribute mapping, or fetch your AppDynamics metadata and JIT-provisioning URL.
| Update SAML Configuration | Fetch SAML Configuration |
|---|---|
|
|