If you run AppDynamics for Databases on a publicly accessible server, or if you'd like to lock down its usage internally, then the simplest solution is to username/password protect access to the UI. You have the option to setup basic security, best for an environment where very few users will have access to the AppDynamics for Databases GUI, or you can integrate AppDynamics for Databases with your LDAP server to grant many users and groups access.toc
Setup Basic Security
AppDynamics for Databases has three predefined users:
...
Note: Do not change the contents of tomcat-users.xml.
...
Implement authentication
...
...
- At the bottom of <AppD4DB
...
- install directory>\apache-tomcat\conf\web.xml, look for the following code:
...
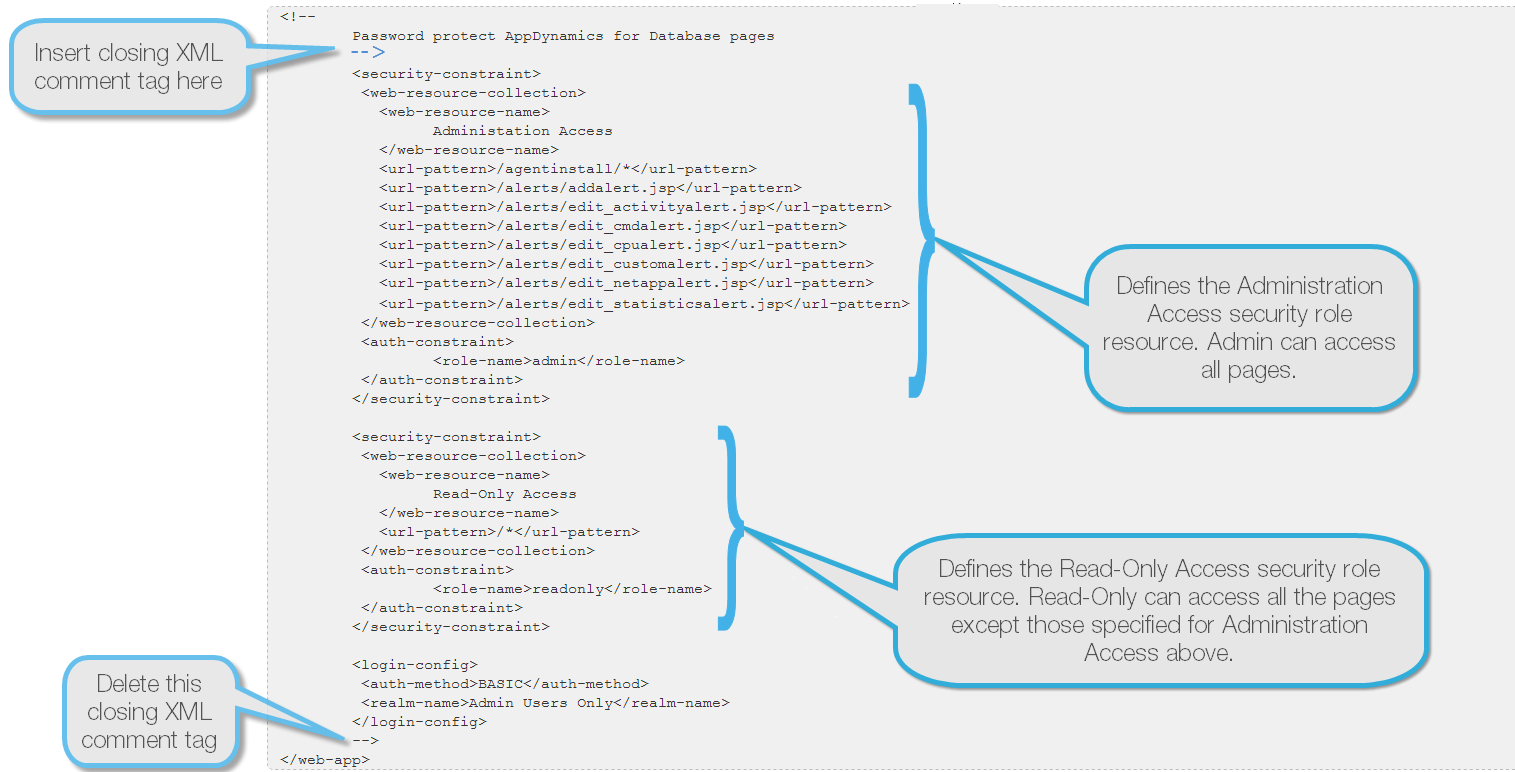 Image Modified
Image Modified
Note: Do not change the contents of web.xml except as instructed below.
...
- Insert a closing XML comment tag after "Password protect AppDynamics for Database pages". The closing XML comment tag
...
- is "
...
- –>".
...
- Remove the closing XML comment tag before "</web-app>". The closing XML comment tag
...
- is "
...
- –>".
...
- Save the file and then restart the AppDynamics for Databases UI service.
- Windows: Go to the Windows services manager and restart "DBTuna GUI".
- Linux: From the AppDynamics for Databases install directory, run the stop.sh script followed by the start.sh script.
...
- In a browser, go to the security page. For example, http://<hostname>:8090/security.
The following dialog appears where you can setup basic security or enable LDAP/Active Directory Service integration for AppDynamics for Databases:
...
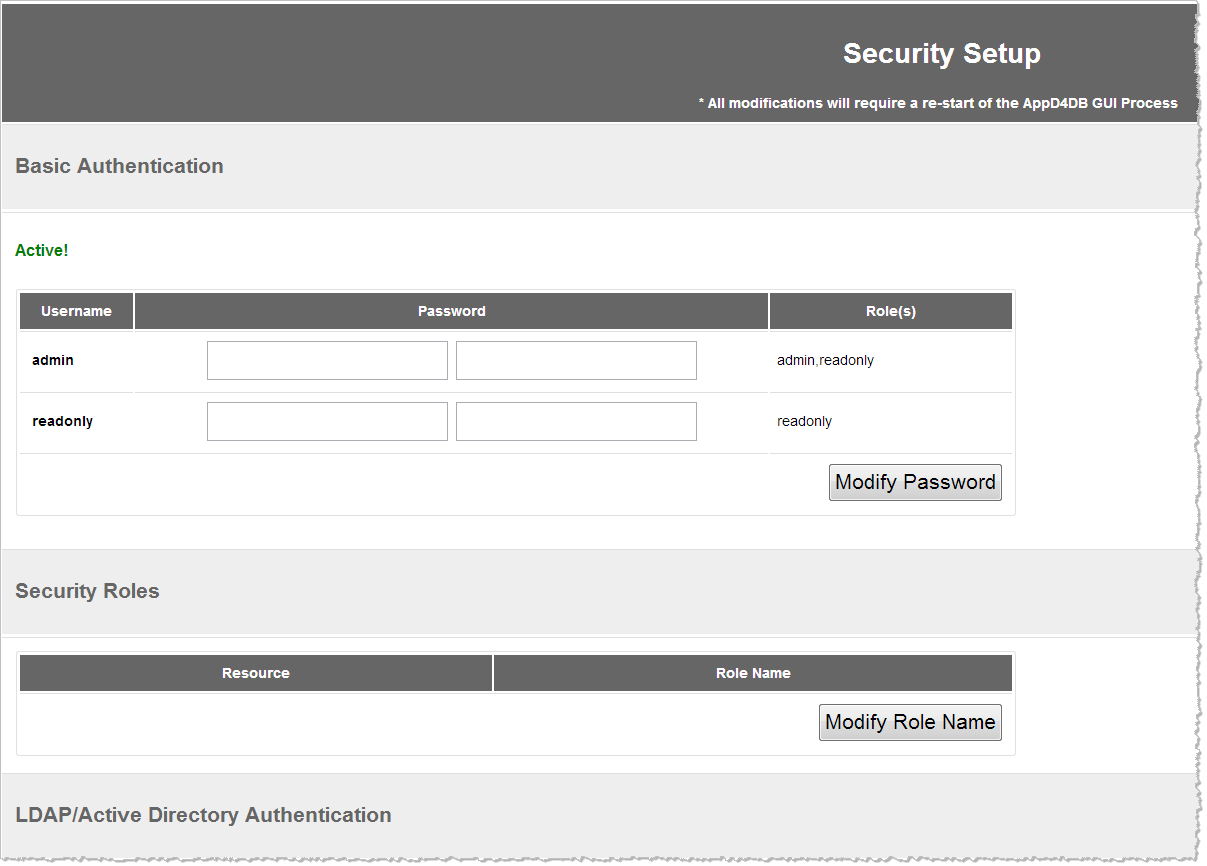 Image Modified
Image Modified
...
- Enter the passwords for the admin and readonly users and then click Modify Password.
...
- To change the password of a user, enter the password twice in the boxes provided and then click Modify Password.
...
- You can change the role name of any of the security roles resources by entering the new Role Name and then clicking Modify Role Name.
When you have security enabled, users must enter the security credentials to access the AppDynamics for Database GUI. The appearance of the logon dialog differs depending on the browser used to access the AppDynamics for Databases GUI. The following is the logon dialog as it appears in Windows Internet Explorer9.
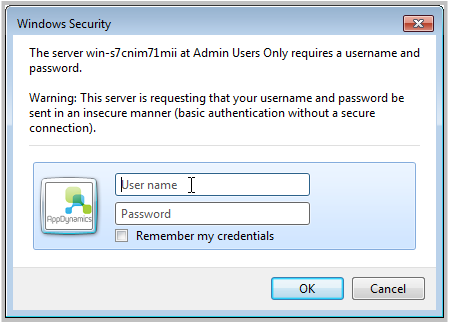 Image Modified
Image Modified
If you enter the wrong username/password combination, the uncompleted logon dialog reappears so you can re-enter your credentials.
If you try to access a page not accessible to the role to which your username has been assigned, you will receive a security violation error.
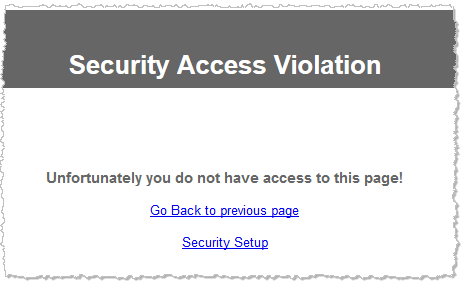 Image Modified
Image Modified
Setup LDAP/Active Directory Integration
When LDAP/Active Directory is integrated, your LDAP and Active Directory users matching the filters defined in this section, will be granted AppDynamics for Databases permissions.
Prerequisite: Setup Basic Security1. Open <AppD4DB
- Open <AppD4DB install
...
- directory>\apache-tomcat\conf\server.xml, locate the line beginning with <!--Realm adCompat... and remove the comment tags from the beginning and end of that line.
...
- Save the file and then restart the AppDynamics for Databases UI service.
- Windows: Go to the Windows services manager and restart "DBTuna GUI".
- Linux: From the AppDynamics for Databases install directory, run the stop.sh script followed by the start.sh script.
...
- In a browser, go to the security page. For example, http://
...
- <hostname>:8090/security.
...
- Scroll down the Security Setup window, you will see the following sections that you must complete and then click Save Config to integrate your LDAP or Active Directory Service server with AppDynamics for Databases.
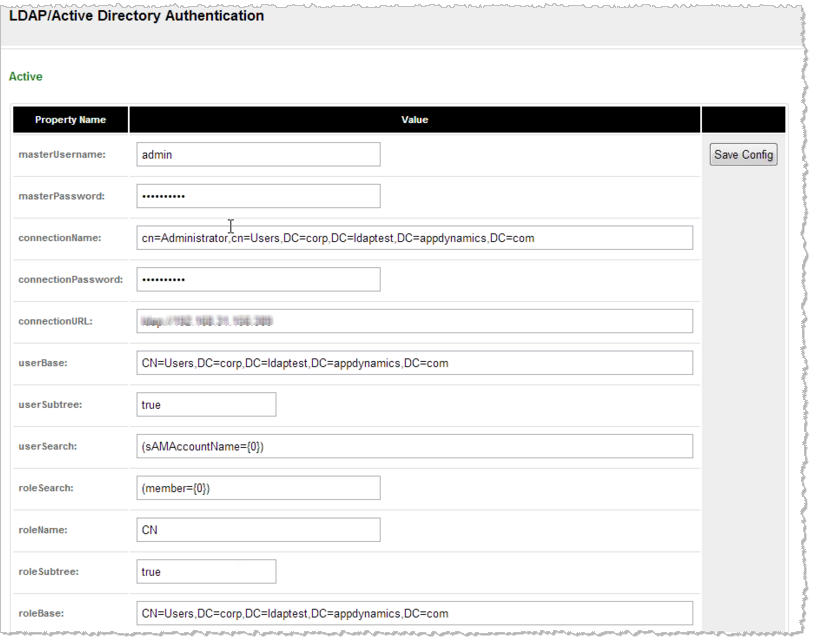 Image Modified
Image Modified
To complete the fields in the LDAP/Active Directory Authentication section
...
- masterUsername: The AppDynamics for Databases user name of the master user or of an administrator.
- masterPassword: The password for the master user.
- connectionName: The user name AppDynamics for Databases uses to log on to the LDAP or Active Directory server.
- connectionPassword: The password for the user AppDynamics for Databases uses to log on to the LDAP or Active Directory server.
- connectionURL: The URL of the LDAP or Active Directory server
- userBase: The starting point for the search for users in the LDAP directory tree. This is referred to as the distinguished name. You can specify the search base using the following comma-separated objects, which are not case-sensitive:
- CN: common name
- OU: organizational unit
- O: organization
- C: country
- DC: domain
- userSubtree: Set this value to "true" to search through the entire user subtree.
- roleSearch: The filter to use for searching groups.
- roleName: The name of the role.
- roleSubtree: Set this value to "true" to search through the entire role subtree.
- roleBase: The starting point for the search for roles.
Enable Authentication Tracking
To log failed and successful logon attempts, add the following code to the end of <AppD4DB install directory>\conf\logging.properties.
| Code Block |
|---|
|
org.apache.catalina.realm.level = ALL
org.apache.catalina.realm.useParentHandlers = true
org.apache.catalina.authenticator.level = ALL
org.apache.catalina.authentical.useParentHandlers = true
|
Monitor Access Attempts
You can check to see who has been successful and unsuccessful attempts to log on to the AppDynamics for Databases UI in the catalina.<date>.log file located in <AppD4DB Install directory>\apache-tomcat\logs. The contents of this file can help you determine whether you have correctly configured the LDAP/Active Directory settings; if the user cannot log on, their logon attempts will show in this file.