Download PDF
Download page Monitor Application Security Using Cisco Secure Application.
Monitor Application Security Using Cisco Secure Application
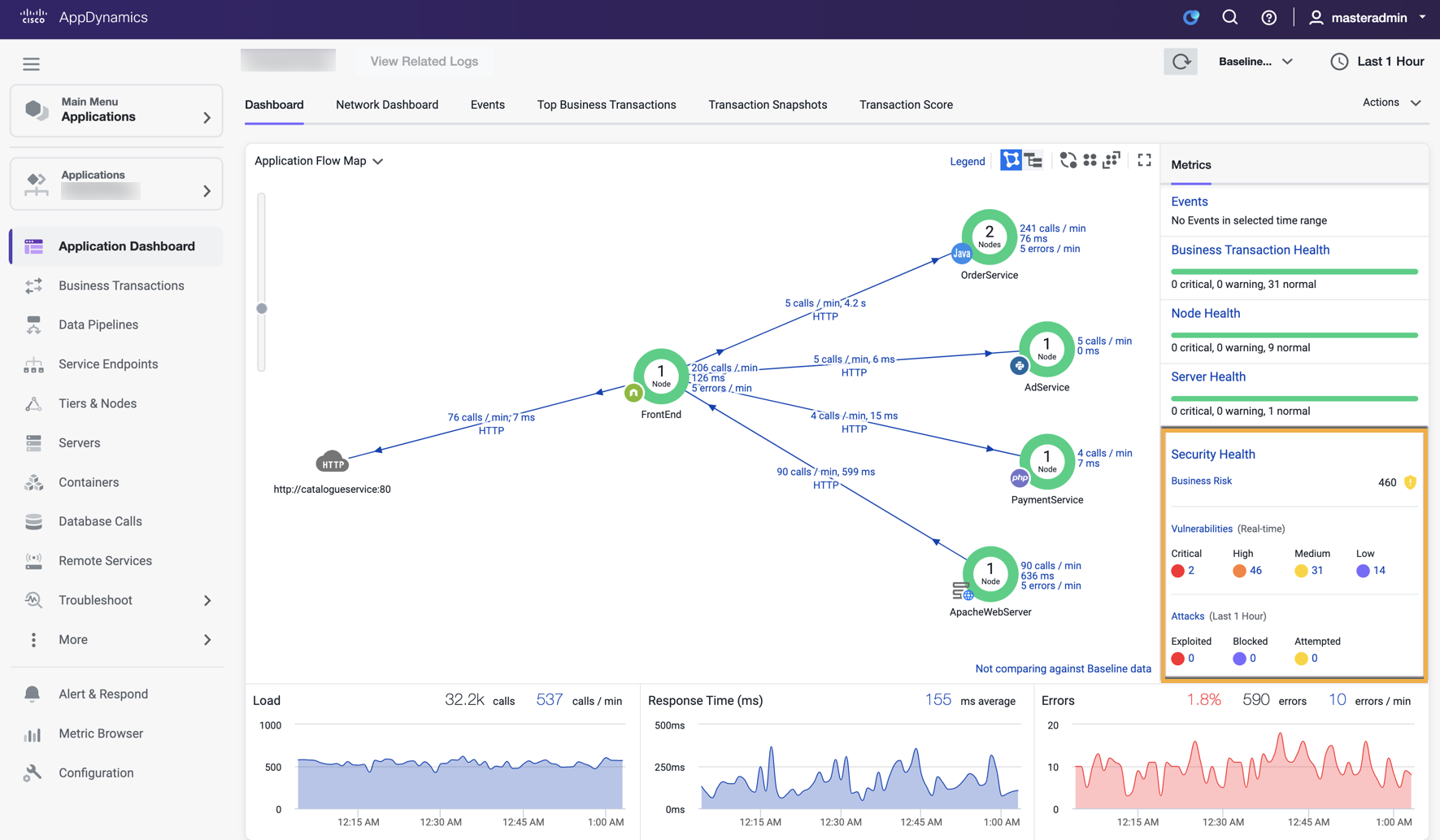
Cisco Secure Application provides a real-time dashboard that provides visibility on the security health of your applications. This dashboard is available when an application is registered with an APM agent and has the appropriate licensing. The agent sends the security events to Cisco Secure Application through the Controller.
The Security Health widget on the Splunk AppDynamics Application dashboard provides high-level information about the security of a registered application. This widget displays the number of critical, warning, and normal security events. To view security details for a selected application on Cisco Secure Application, click the Security Health widget.
Select Scope for the Dashboard
Cisco Secure Application dashboard provides a Global Filter to select the required application and tier scope that is applied across all views within this dashboard except Policies. By default, the application scope is the selected application on the Splunk AppDynamics dashboard prior to navigating to Cisco Secure Application.
To view the data on the dashboard for a specific application:
- From the Cisco Secure Application dashboard, click Select.
- In the Filter by Application tab, search for the specific application.
- Select the application.
- (Optional) In the Filter by Tier tab, search for the required tier.
If you do not select any specific tier, then data is displayed for all the tiers. - Click Apply.
Navigate to Cisco AppDynamics Application or Tier Flow Map
To navigate from the Cisco Secure Application dashboard to the Splunk AppDynamics flow map, click the flow map icon (![]() ) that appears on these pages: Applications, Business Transactions, Libraries, Attacks. The flow map icon is associated with the selected scope for the Cisco Secure Application dashboard. See Select Scope for the Dashboard.
) that appears on these pages: Applications, Business Transactions, Libraries, Attacks. The flow map icon is associated with the selected scope for the Cisco Secure Application dashboard. See Select Scope for the Dashboard.
View Data Using Search Filter
The Cisco Secure Application provides a Search filter on various pages in the dashboard. The search filter allows you to search based on a selected category. For example, on the Business Transaction page, you can search by Business Transaction, Application, and Entry Tier.
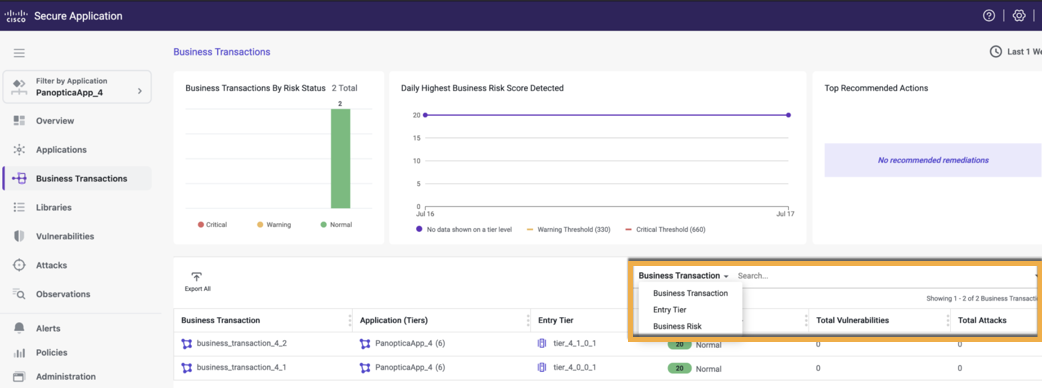
You can select the required search category from the dropdown list, then click the Search field to view the list of values corresponding to the category. You can also find the required value as you type. If you do not require the exact match, you can enter the required generic value in the Search field. For example, consider that you want to search for all applications that start with a specific prefix, AD. You can select the search category as Application and enter AD in the Search field.
You can search using one or all the categories, but each category can have a single search value. A category is disabled when you specify a search value for that category, but you can continue to select another available category and specify its search value. These search values act as filters. You can remove the search values to remove the search filter.
Navigate to the Cisco Secure Application Dashboard
Cisco Secure Application provides a real-time dashboard that displays these pages:
- Overview: This page provides an overall overview of attacks and vulnerabilities of monitored applications. See Overview of Cisco Secure Application.
- Applications: This page provides the details of monitored nodes that are registered with Cisco Secure Application for the managed applications. See Monitor Security Status of Applications.
- Business Transactions: This page includes details to monitor the vulnerability risk of a business transaction. See Monitor Business Transactions.
- Libraries: This page provides details of the existing libraries that require remediation. See Monitor Libraries.
- Vulnerabilities: This page provides information about all discovered vulnerabilities. See Monitor Vulnerabilities.
- Attacks: This page provides information about all detected attacks. See Monitor Attacks.
- Observations: This page provides information to investigate incidents and define the runtime policy. See Monitor Observations.
- Policies: This page allows you to create or customize the policies for vulnerabilities and attacks. See Cisco Secure Application Policies.