Download PDF
Download page Monitor Libraries.
Monitor Libraries
The Libraries page provides a list of all libraries that are in use by the corresponding applications. The page highlights the vulnerabilities and associated risks introduced by the use of those libraries.
- You can use the Search filter for the Application, Package Language, Tiers, Status, and Libraries categories. For information about the Search filter, see View Data Using Search Filter in Monitor Application Security Using Cisco Secure Application.
- The Set Status and Edit Note bulk edit options are available if you have the Configure Cisco Secure Application permission.
Libraries includes these details:
| Field Name | Description |
|---|---|
| Library | Libraries in the selected application. You can click on the row to view the details of the library. See View Vulnerabilities for a Library. |
| Application | The application name that uses the corresponding library. |
| Tier (Nodes) | The application tier that is vulnerable because of its relationship to the corresponding library. Click the flow map icon ( |
| Risk | The risk score given to the library. This helps to identify which libraries require immediate remediation. The higher the risk score, the higher the impact of the collection of vulnerabilities within the library. Click this field to sort the risk score from high to low or low to high. |
| Vulnerabilities | The number of vulnerabilities based on severity. Severity is represented with these colors:
Hover on the required color to know the severity. If any of the preceding colors are replaced with the grey color, it indicates that there are no vulnerabilities of that specific severity. For example, Vulnerabilities display the grey, orange, yellow, and purple colors instead of the red, orange, yellow, and purple colors. Here, the red color is replaced with the grey color. This indicates that there are no critical vulnerabilities. Click this field to sort in increasing or decreasing order based on the number of vulnerabilities. |
| Remediation | The recommended version of the library that can be used for remediation. |
| Status | The status of the vulnerable libraries. By default, when a vulnerability is detected the value is Detected. The status value can be:
The Detected, Downgraded, and Upgraded status are auto-populated. If you have the Configure Cisco Secure Application permission, you can change the Status by selecting the required libraries and using the Set Status option. You must have the configure permission to view and use the Set Status option. Click this field to sort based on the status of the vulnerable library. |
| Note | Notes can be used to share information with other users or document findings during the review of a vulnerability. If you have the Configure permission, you can add notes by selecting a library and using the Edit Note option. Without the Configure permission, the Edit Note option is unavailable. |
You can click the Export button to download the table data. It downloads all of the rows, columns, and related data in a .csv file. A separate .json file includes the following: link to the Cisco Secure Application website where the table is exported from, global filters (if any) applied to the pages, and search filters applied to the columns. These two files are compressed into a .zip file for downloading. The maximum number of rows that can be exported is 10,000. If table data exceeds 10,000 rows you may apply filters to narrow your search, or export the first 10,000 results.
View Vulnerabilities for a Library
To view all the vulnerabilities within a specific library, click the row on the Libraries page. This directs you to the library details page with the following information:
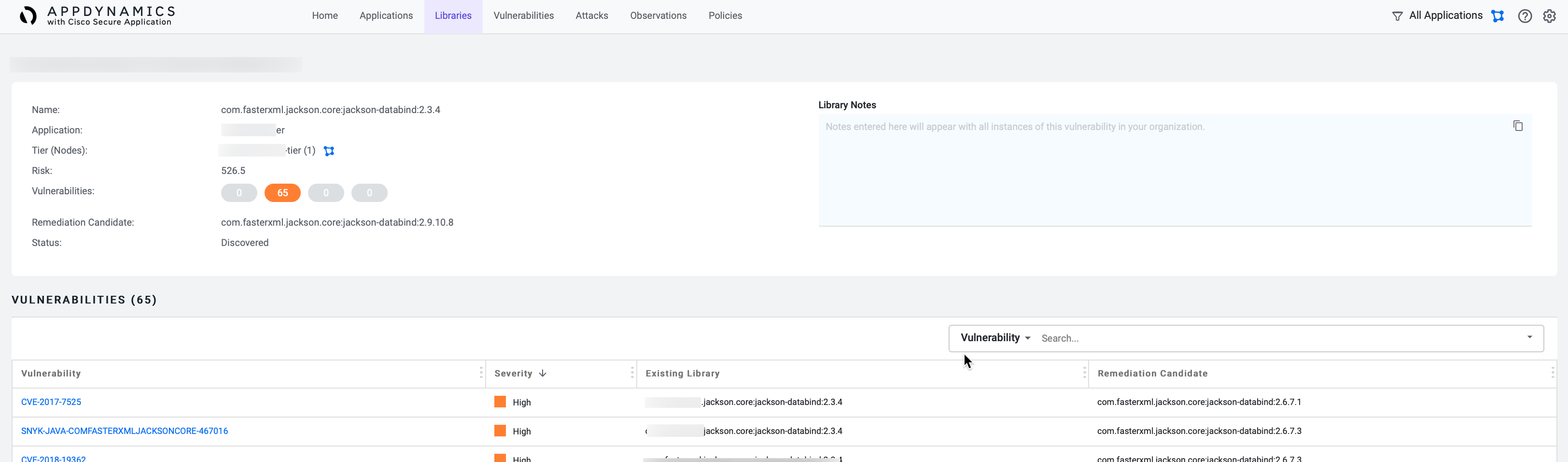
The upper pane displays the details about the vulnerable library, which includes these fields:
| Field Name | Description |
|---|---|
| Application | The name of the application that uses the selected library. |
| Tier (Nodes) | Name of the affected tier. You can click the flowmap icon ( The number in the parenthesis () indicates the number of affected nodes. |
| Type | The language used for the corresponding library. Currently, Cisco Secure Application supports Java and .NET. |
| Risk | The risk score for this library. This field is unavailable when the library is fixed (upgraded or downgraded to the required version), removed, or not vulnerable. |
| Status | The status of the library. |
The bottom pane provides the following details:
You can use the Search filter to view the vulnerability details list based on the Severity or the Vulnerability value. For more information about the Search filter, see View Data Using Search Filter in Monitor Application Security Using Cisco Secure Application.
| Field Name | Description |
|---|---|
| Severity | The severity of the vulnerability. Click the field to sort the severity in alphabetical order. |
| Reached | A yellow icon is displayed in this column to indicate that a vulnerability method is matched. |
| Risk | The risk score for this library. This field is unavailable when the library is fixed (upgraded or downgraded to the required version), removed, or not vulnerable. |
| Title | The vulnerability type associated with the library. |
| ID | The Common Vulnerabilities and Exposure (CVE) identifier. Click the CVEs to view the vulnerability details. For information about Vulnerabilities, see Monitor Vulnerabilities. |
| Current Library | The library that introduced the vulnerability to the application. |
| Remediation Candidate | The version of the library that should be used to remediate the vulnerability. |
You can click the Export button to download the table data. It downloads all of the rows, columns, and related data in a .csv file. A separate .json file includes the following: link to the Cisco Secure Application website where the table is exported from, global filters (if any) applied to the pages, and search filters applied to the columns. These two files are compressed into a .zip file for downloading. The maximum number of rows that can be exported is 10,000. If table data exceeds 10,000 rows you may apply filters to narrow your search, or export the first 10,000 results.