Download PDF
Download page Map SAML Group to Cisco AppDynamics Roles - SaaS.
Map SAML Group to Cisco AppDynamics Roles - SaaS
This page describes configuring Security Assertion Markup Language (SAML) attributes to role mapping and the SAML group attribute value mapping options in your Splunk AppDynamics SaaS environment.
If the identity assertion from the SAML provider includes group names that correspond to Splunk AppDynamics roles, you can configure mappings between those group names and the roles. Navigate to Settings![]() > Administration > Authentication Provider to access the SAML Group Mappings that control the mappings.
> Administration > Authentication Provider to access the SAML Group Mappings that control the mappings.
Once users are in the system, you can assign roles directly to them. See Map SAML Group to Cisco AppDynamics Roles - SaaS. You can also configure group attributes from SAML Group Mapping for role mapping and default role assignment.
Configure SAML Attribute to Role Mapping
To configure the SAML attribute to role mapping:
In the SAML Group Attribute Name field, enter the
Nameattribute value that identifies the SAML Attribute element with group affiliations for the user. For example, given the following response snippet, useSAML groups-Membershipin the SAML Group Attribute Name field.<saml:Attribute NameFormat="urn:oasis:names:tc:SAML:2.0:attrname-format:basic" Name="Groups-Membership"> <saml:AttributeValue xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance" xsi:type="xs:string"> {group1};{group2} </saml:AttributeValue> </saml:Attribute>XML- Use the Group Attribute Value and Mapping of Group to Roles settings to describe the structure of the SAML group attribute from which Splunk AppDynamics needs to extract the group value and the roles associated with those values. The Controller Tenant can extract Group Attribute values based on the following options:
- Singular Group Values—the response contains an
AttributeValueelement with a single group-mapping value. - Multiple Nested Group Values—the response contains more than one
AttributeValueelement, each with a single group-mapping value. - Singular Delimited Group Value—the response contains one
AttributeValueelement with multiple, delimiter-separated group-mapping values. - Regex on Singular Group Value—the response contains a single
AttributeValueelement from which you want to extract the group-mapping value with a regular expression.
- Singular Group Values—the response contains an
- If the group attribute value returns in LDAP format, select the Value is in LDAP Format checkbox. For example: when
OU=AppDynamics-Usersis enabled, onlyAppDynamics-Usersmaps to the SAML Group name.
SAML Group Mappings
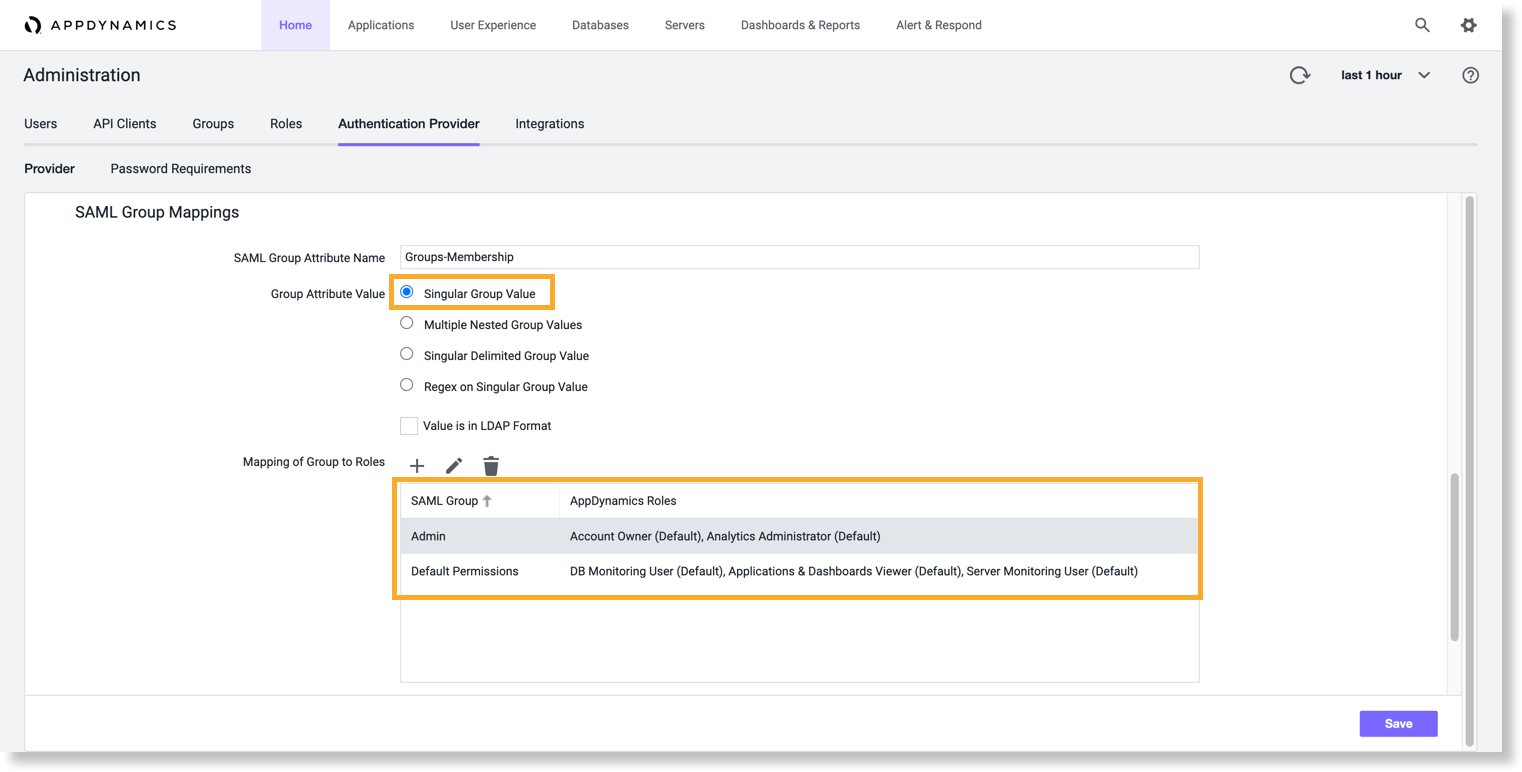
Singular Group Values
Select Singular Group Value if the SAML group attribute contains a single group.
<saml:AttributeStatement>
<saml:Attribute Name="Groups-Membership" NameFormat="urn:oasis:names:tc:SAML:2.0:attrname-format:basic">
<saml:AttributeValue xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance" xsi:type="xs:string">Admin</saml:AttributeValue>
</saml:Attribute>
</saml:AttributeStatement>For this example, Splunk AppDynamics would extract the value Admin and associate the user with a SAML Group with the same name. In this sample configuration, the user would get the configured roles assigned to the Admin SAML group, such as Account Owner and Analytics Administrator.
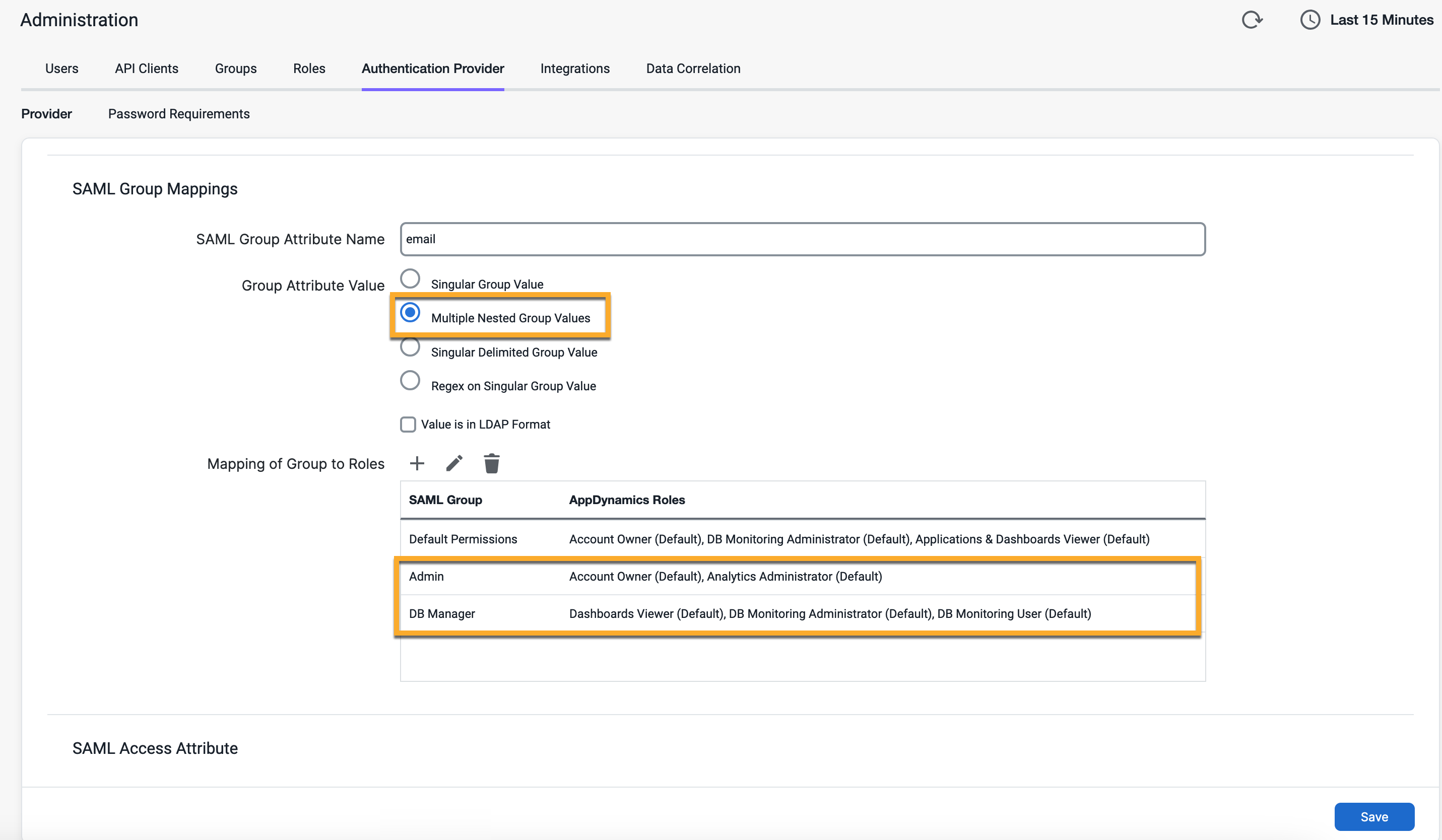
Multiple Nested Group Values
When you select this option, Splunk AppDynamics expects multiple AttributeValue child elements under the SAML Attribute with the group information.
<saml:Attribute Name="Groups-Membership" NameFormat="urn:oasis:names:tc:SAML:2.0:attrname-format:basic">
<saml:AttributeValue xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance" xsi:type="xs:string">_Admin_</saml:AttributeValue>
<saml:AttributeValue xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance" xsi:type="xs:string">_DBManager_</saml:AttributeValue>
</saml:Attribute> Splunk AppDynamics would extract _Admin_ and _DBManager_ from the example. In this sample configuration, the user with the previous response would receive the roles from the _Admin_ and _DBManager_ groups.
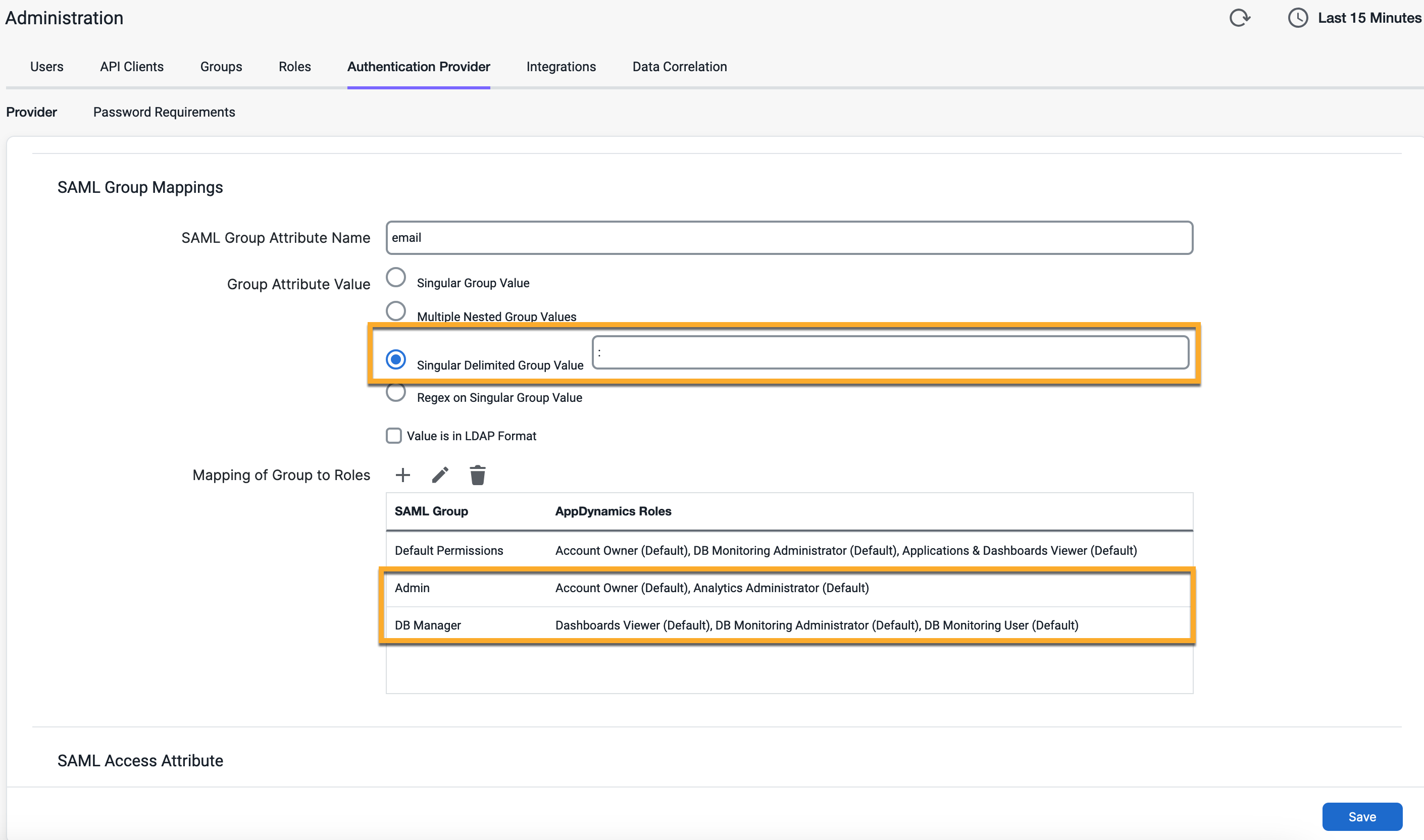
Singular Delimited Group Value
When you select this option, Splunk AppDynamics expects a single AttributeValue element with multiple, delimiter-separated values.
<saml:Attribute Name="Groups-Membership" NameFormat="urn:oasis:names:tc:SAML:2.0:attrname-format:basic">
<saml:AttributeValue xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance" xsi:type="xs:string">Admin;DB-Manager</saml:AttributeValue>
</saml:Attribute>Specify the delimiter that separates the values to extract, such as a semi-colon.
In this sample configuration, the user would get the Splunk AppDynamics roles that associate with both the Admin and DB-Manager groups, such as the Dashboard Viewer, User, and DB Monitoring Administrator.
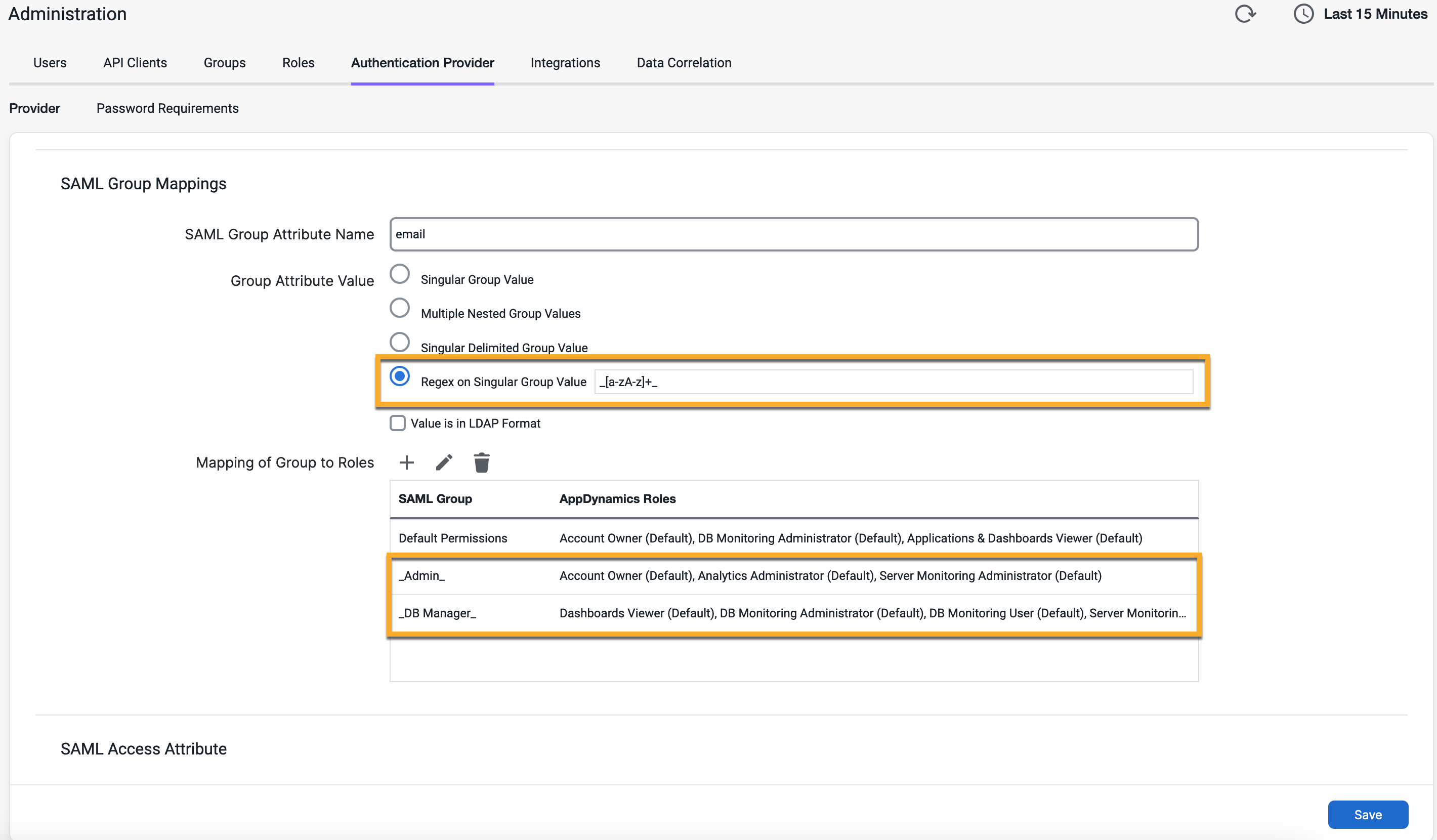
Regex on Singular Group Value
Choose this option to have Splunk AppDynamics extract group mapping values using a regular expression. Regular expressions enable you to pull group values from unstructured contexts, such as from within a larger string.
<saml:AttributeStatement>
<saml:Attribute Name="Groups-Membership" NameFormat="urn:oasis:names:tc:SAML:2.0:attrname-format:basic">
<saml:AttributeValue xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance" xsi:type="xs:string">User memberships in _Admin_ and _DBManager_ groups.</saml:AttributeValue>
</saml:Attribute>
</saml:AttributeStatement>In this example, the group names _Admin_ and _DBManager_ are embedded in the AttributeValue string. To extract those names, you can use a regular expression such as _[a-zA-Z]_. Like other types of group attribute sources, Splunk AppDynamics assigns all roles associated with both the _Admin_ and _DBManager_ SAML Groups.